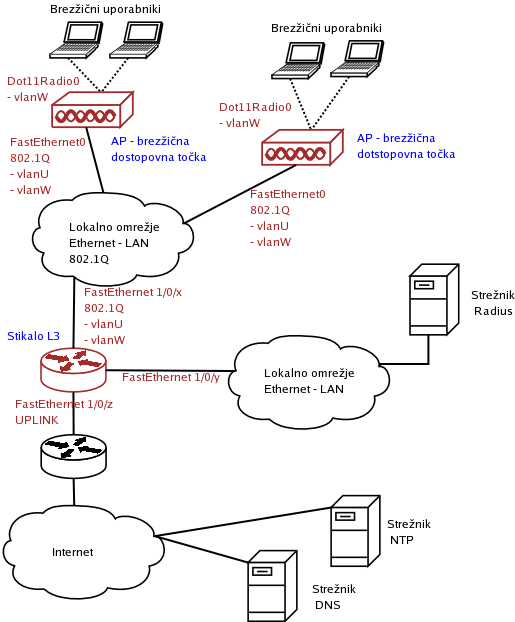
Kratek povzetek nastavitev
- Do AP je potrebno vzpostaviti snop VLANov 802.1Q.
- VLANe se zaključi (dodeli se jim L3 vmesnik IP) na stikalu in nanj se nastavi filtre IP v skladu z varnostno politiko organizacije.
- Priporočljivo je, da se za upravljalno omrežje (angl. managment network) uporabi precej omejujoče filtre. Upravljalni dostop (TFTP, FTP, SSH, telnet in SNMP) naj bi bil dovoljen izključno delovnim postajam za upravljanje omrežja ter za protokole NTP in DNS z ustreznih strežnikov.
- Priporočljivo je, da se na vse vmesnike doda zaščitna pravila proti ponarejanju izvornega naslova IP (t.i. pravila "anti-spoofing").
- Tu navedeni filtri so le osnovni, priporočeni. Vsaka organizacija si naj filtre prilagodi glede na svojo varnostno politiko omrežja.
- Začetne ključe RSA za delovanje storitve SSH se zgenerira z ukazom: crypto key generate rsa. Zgenerirajte ključ velik vsaj 1024 bitov.
- Na vseh vlanih do AP se vkljuci DHCP Snooping ter Dynamic ARP inspection. Na vmesnikih do uporabnikov (AP) se vkljuci se ip verify source. Delovanje DHCP snooping se preveri z: show ip dhcp snooping binding. Z ukazom terminal monitor pa se vkljuci spremljanje dnevnika v katerega se med drugim beležijo tudi zavrnitve pri preverjanju paketov ARP.
Vzorčna nastavitev
Nastavitev vmesnika s povezavo UPLINK:
interface GigabitEthernet0/1
description UPLINK
ip address <naslov IPv4> 255.255.255.254
ipv6 address <naslov IPv6>/126
no switchport
ip access-group ProtectWAN4 in
ipv6 traffic-filter ProtectWAN6 in
!
Pripadajoči vhodni filtri vmesnika UPLINK:
Pozor! Pri maskah omrežij v filtrih ne smemo pozabiti, da so inverzne (npr.: za masko 255.255.255.192 se vnese maska 0.0.0.63).
ip access-list extended ProtectWAN4
remark === Block traffic from private IPs ===
deny ip 10.0.0.0 0.255.255.255 any
deny ip 127.0.0.0 0.255.255.255 any
deny ip 172.16.0.0 0.15.255.255 any
deny ip 192.168.0.0 0.0.255.255 any
remark === allow all IP traffic from UPLINK peer and MANAGMENT NETWORK ===
permit ip host <Naslov IP sosednjega stikala - peer> any
permit ip <naslov nadzornega omrežja> <maska omrežja> any
remark === Allow DNS and NTP from servers ===
permit udp host <Strežnik DNS> eq domain any gt 1023
permit tcp host <Strežnik DNS> eq domain any gt 1023 established
permit udp host <Strežnik NTP> eq ntp
remark === allow certain ICMP types to UPLINK interface ===
permit icmp any host <Naslov IP uplink>
permit udp any host <Naslov IP uplink> range 33434 33523
Za vsak vmesnik VLAN/omrežje na stikalu dodamo sledeči kos filtra:
remark === allow ICMP to vlan? GW and deny all other traffic ===
permit icmp any host <Naslov IP na vmesniku vlan?>
permit udp any host <Naslov IP na vmesniku vlan?> range 33434 33523
deny ip any host <Naslov IP na vmesniku vlan?>
remark === allow traffic to vlan? network ===
permit ip any <Naslov omrežja vlan?> <maska omrežja>
Temu sledi še zadnji kos filtra, ki omejuje in logira ves preostali promet:
remark === drop other traffic with logging ===
deny ip any any log
!
Nastavitev vmesnika, kamor se priklopi streznik DHCP (angl. Dynamic Host Configuration Protocol)
Enake nastavitve lahko uporabimo tudi za druge segmente omrežja Ethernet, ki mu zaupamo (strežniki, stikala z vključenimi zaščitami L2).
<vlanU> je številka upravljalnega (angl. management) vlana,
<vlanW> je številka vlana za brezžične uporabnike:
interface GigabitEthernet0/<stevilka vmesnika s streznikom DHCP>
description Streznik DHCP
switchport access vlan <vlanStrezniki>
ip arp inspection trust
ip dhcp snooping trust
!
Nastavitev vmesnika, kamor se priklopi dostopovna točka (angl. AP - Access Point).
<vlanU> je številka upravljalnega (angl. management) vlana,
<vlanW> je številka vlana za brezžične uporabnike:
interface GigabitEthernet0/<številka vmesnika do AP>
description AP - Soba 23
switchport trunk encapsulation dot1q
switchport trunk allowed vlan <vlanU>,<vlanW>
switchport mode trunk
ip verify source port-security
!
interface Vlan<vlanU>
description Upravljalni VLAN
ip address <Prehod IPv4> <maska omrežja>
ip access-group SanitizeAP in
ip access-group ProtectAP out
!
interface Vlan<vlanW>
description Omrezje IPv4 in IPv6 za brezžične uporabnike
ip address <Prehod IPv4> <maska omrežja>
ip access-group SanitizeEduroam in
ip access-group ProtectEduroam out
ip helper-address <naslov strežnika DHCP>
ipv6 enable
ipv6 address <Prehod IPv6>/64
ipv6 traffic-filter SanitizeEduroam6 in
ipv6 traffic-filter ProtectEduroam6 out
ipv6 nd prefix <Prefix6>/64
ipv6 nd router-preference High
ipv6 nd ra lifetime 3600
ipv6 nd ra interval 60 15
!
ip routing
ipv6 unicast-routing
ip dhcp snooping
ip dhcp snooping vlan <vlanU>
ip dhcp snooping vlan <vlanW>
ip arp inspection vlan <vlanU>
ip arp inspection vlan <vlanW>
Za vsako napravo s statičnim naslovom IP (kot je na primer AP - dostopovna točka) na vmesniku, ki ga varuje "ip verify source port-security" se vnese vrstico "ip source binding". S tem se vnese statični vpis in za ustrezno napravo ni nujen vnos v tabeli vnosov DHCP (angl. DHCP Snooping bindings):
ip source binding <Naslov MAC> vlan <vlanU> <AP IP> interface <vmesnik do AP>
Filtri za promet upravljalnega omrežja vlanU
Pozor! Pri maskah omrežij v filtrih ne smemo pozabiti, da so inverzne (npr.: za masko 255.255.255.128 se vnese maska 0.0.0.127).
Dohodni promet (izhodni na vmesniku stikala):
ip access-list extended ProtectAP
remark === Block traffic from private IPs ===
deny ip 10.0.0.0 0.255.255.255 any
deny ip 127.0.0.0 0.255.255.255 any
deny ip 172.16.0.0 0.15.255.255 any
deny ip 192.168.0.0 0.0.255.255 any
remark === Allow all traffic from MANAGMENT NETWORK ===
permit ip <naslov nadzornega omrežja> <maska omrežja> any
remark === Allow DNS and NTP from servers ===
permit udp host <Strežnik DNS> eq domain <Naslov omrežja vlanU> <maska> gt 1023
permit tcp host <Strežnik DNS> eq domain <Naslov omrežja vlanU> <maska> gt 1023 established
permit udp host <Strežnik NTP> <Naslov omrežja vlanU> <maska> eq ntp
remark === drop other traffic with logging ===
deny ip any any log
!
Izhodni promet (t.i.: anti-spoofing, vhodni na vmesniku stikala):
ip access-list extended SanitizeAP
remark === Block traffic from private IPs ===
deny ip 10.0.0.0 0.255.255.255 any
deny ip 127.0.0.0 0.255.255.255 any
deny ip 172.16.0.0 0.15.255.255 any
deny ip 192.168.0.0 0.0.255.255 any
remark === allow valid traffic from vlanU network ===
permit ip <Naslov omrežja vlanU> <maska omrežja> any
remark === drop other traffic with logging ===
deny ip any any log
!
Filtri za promet brezžičnega omrežja vlanW
Dohodni promet (izhodni na vmesniku stikala):
ip access-list extended ProtectEduroam
remark === Block traffic from private IPs ===
deny ip 10.0.0.0 0.255.255.255 any
deny ip 127.0.0.0 0.255.255.255 any
deny ip 172.16.0.0 0.15.255.255 any
deny ip 192.168.0.0 0.0.255.255 any
remark === Block spoofed IPs, this kills further subnetting ===
deny ip <Naslov omrežja vlanW> <maska omrežja> any
remark === Allow all traffic to network ===
permit ip any <Naslov omrežja vlanW> <maska> established
remark === Drop and log everything else ===
deny ip any <Naslov omrežja vlanW> <maska omrežja> log
!
ipv6 access-list ProtectEduroam6
remark === Block traffic from prohibited addresses ===
deny ipv6 2001:DB8::/32 any
remark === neighbor discovery ===
permit icmp FE80::/10 FE80::/10 nd-na
permit icmp FE80::/10 FF02::/16 nd-ns
remark === Block spoofed IPs ===
deny ipv6 i<prefix>/64 any
remark === Allow all traffic to network ===
permit ipv6 any <prefix>/64
remark === Drop and log everything else ===
deny ipv6 any any log
!
Izhodni promet (t.i.: anti-spoofing, vhodni na vmesniku stikala):
ip access-list extended SanitizeEduroam
remark === Block traffic from private IPs ===
deny ip 10.0.0.0 0.255.255.255 any
deny ip 127.0.0.0 0.255.255.255 any
deny ip 172.16.0.0 0.15.255.255 any
deny ip 192.168.0.0 0.0.255.255 any
remark === allow DHCP requests from vlanW network ===
permit udp host 0.0.0.0 eq bootpc host 255.255.255.255 eq bootps
remark === allow valid traffic from vlanW network ===
permit ip <Naslov omrežja vlanW> <maska omrežja> any
remark === drop other traffic with logging ===
deny ip any any log
!
ipv6 access-list SanitizeEduroam6
remark === permit local traffic - neighbor discovery ===
permit ipv6 FE80::/10 any
remark === allow valid traffic from network ===
permit ipv6 <prefix>/64 any
remark === Drop and log everything else ===
deny ipv6 any any log
!

